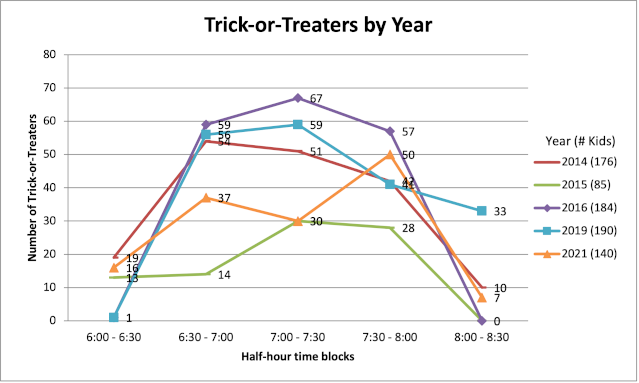
How to Manually Upgrade Rosetta
Rosetta is used to enable a Mac with Apple silicon to use apps built for Intel. Most of the time, you’ll get prompted to install it the first time you need it and after that the automatic software update process will take over. However, in some environments the automatic mechanisms don’t work - maybe it’s incorrectly blocked or the update isn’t detecting things right. Here’s how to update Rosetta manually.
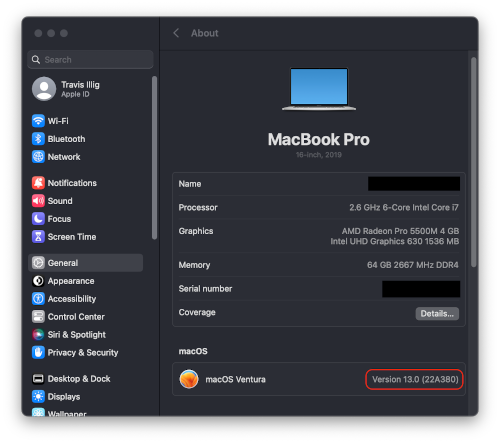
First, get your OS build number: 🍎 -> About This Mac -> More Info.
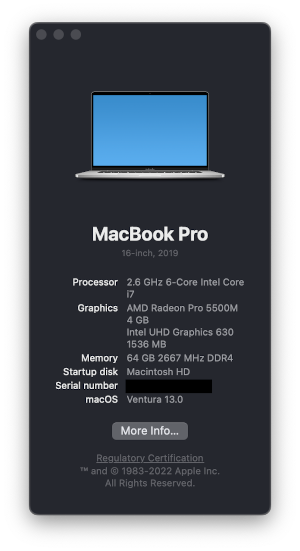
Click on the Version XX.X field and it should expand to show you the build number. It will be something like 22A380.
Go to the software catalog for Rosetta and search for your build number. You should see your build-specific package. The build number is in ExtendedMetaInfo:
<dict>
<key>ServerMetadataURL</key>
<string>https://swcdn.apple.com/content/downloads/38/00/012-92132-A_1NEH9AKCK9/k8s821iao7kplkdvqsovfzi49oi54ljrar/RosettaUpdateAuto.smd</string>
<key>Packages</key>
<array>
<dict>
<key>Digest</key>
<string>dac241ee3db55ea602540dac036fd1ddc096bc06</string>
<key>Size</key>
<integer>331046</integer>
<key>MetadataURL</key>
<string>https://swdist.apple.com/content/downloads/38/00/012-92132-A_1NEH9AKCK9/k8s821iao7kplkdvqsovfzi49oi54ljrar/RosettaUpdateAuto.pkm</string>
<key>URL</key>
<string>https://swcdn.apple.com/content/downloads/38/00/012-92132-A_1NEH9AKCK9/k8s821iao7kplkdvqsovfzi49oi54ljrar/RosettaUpdateAuto.pkg</string>
</dict>
</array>
<key>ExtendedMetaInfo</key>
<dict>
<key>ProductType</key>
<string>otherArchitectureHandlerOS</string>
<key>BuildVersion</key>
<string>22A380</string>
</dict>
</dict>
Look for the URL value (the .pkg file). Download and install that. Rosetta will be updated.